
I helped a client recover from a nightmare hack when she lost 40,000 email subscribers. Three days of her life disappeared into damage control, her reputation took a hit, and she’s still recovering.
But here’s the thing. Within 3 hours of implementing proper security, we bulletproofed her site. Two years later? Zero successful attacks, her search rankings improved, and customer trust came back stronger.
That success got me thinking about something important.
I recently created a WordPress speed and performance checklist after many users asked for a compact resource they could follow step by step.
I then realized that WordPress security and performance solve the same core problems. Both keep your site stable, prevent crashes, and downtime. Both protect your search rankings.
A fast site is often a secure site. A secure site stays fast because it’s not battling malware or attack traffic.
So today, I’m giving you the security companion to that performance guide. Think of this as the second half of keeping your WordPress site healthy and running smoothly.
In 40 minutes, your site will be more secure than 80% of WordPress sites out there. No scary jargon. No expensive enterprise tools. Just smart, systematic protection that actually works.
In fact, for each step, I show you the manual approach and a free tool that can help you improve your security.
Quick Takeaways: What You’re Getting Today
- Automatic backups protecting your entire site
- Login defenses blocking 99% of attacks
- Real-time monitoring catching threats early
- WordPress core locked down against exploits
- Professional firewall running for free
Time investment: 40 minutes. Protection: Years.
Understanding What You’re Protecting Against (5 Minutes)
Before throwing security plugins at your site, spend 5 minutes understanding what actually threatens WordPress sites.
This knowledge helps you make smart decisions, not panicked ones.
See, most beginners install every security plugin they find and enable every feature. As a result, their site slows to a crawl, and they still don’t know what they’re actually protecting against.
The Real Numbers (2025-2026)
WordPress sites face attacks every 32 minutes on average.
That sounds scary. But here’s the reality: 96% of vulnerabilities live in plugins, not WordPress itself. WordPress core is incredibly secure. Your plugins? That’s where the problems hide.
Plus, according to Search Engine Journal, 55% of all attacks are SEO spam.
Not dramatic movie-style hacking with hooded figures typing furiously. Just automated bots injecting hidden spam pages to hijack your search rankings.
Only 27% of site owners have proper recovery plans.
That last number matters most because most hacks are recoverable if you’re prepared. And that is why we are here today. To help you stop WordPress security attacks before they happen.
The 3 Most Common Attacks (What Actually Happens)
1. Brute Force Login Attacks
Brute force security attacks happen when bots try thousands of password combinations on your login page. They’re not targeting you specifically. Instead, they’re hitting every WordPress site they can find.
Meaning, if your site is protected or needs extra work to hack it, they just skip over it. After all, they can target millions of other sites.
Check out this post to learn everything you need to know about brute force attacks.
The good news? This is fixed in 2 minutes with simple tools you’ll install shortly.
2. Outdated Plugin Exploits
Old plugins become unlocked doors into your site. Hackers scan for sites running vulnerable plugin versions. When they find one, automated tools exploit the known vulnerability.
3. SEO Spam Injection
Attackers inject hidden content to boost their own search rankings.
They create thousands of spam pages on your domain. Google sees these pages, which results in your rankings tanking. In the end, visitors get redirected to scam sites.
Now, if you want to quickly see the status of your site and if any of these vulnerabilities are on your site, start by scanning your site with our free WordPress security checker.
Complete WordPress Security Checklist
Now, I know that this is a long post and you can easily get confused. So I have condensed the entire checklist using the table of contents below. This way, you can see everything at a glance.
Plus, you can skip to any part of the WordPress security checklist by using the links below.
- ☐ Emergency Foundation – Do This First (10 Minutes)
- ☐ Enable Strong Authentication (2 minutes)
- ☐ Install Your Security Plugin (3 minutes)
- ☐ Verify Your Hosting Security (2 minutes)
- ☐ Lock Down User Access (3 minutes)
- ☐ Clean Up Your Plugins (4 minutes)
- ☐ Limit Login Attempts and Device Access (3 minutes)
- ☐ Secure WordPress Core Files (4 minutes)
- ☐ Clean and Protect Your Database (2 minutes)
- Advanced Protection Layer (8 Minutes)
- Common Beginner Mistakes (And How to Avoid Them)
- FAQ: WordPress Security Checklist
- Final Verdict: How Important Is WordPress Security for Your Business?
With that out of the way, let us get into our security checklist!
☐ Emergency Foundation – Do This First (10 Minutes)
These four things are your safety net. Not glamorous, but they’ll save your site when disaster strikes.
You’re already more secure than 70% of WordPress sites after this section.
Set Up Automated Backups (3 minutes)
Like with house insurance, you hope you never need it, but when you do and do not have it, it can be disastrous.
The reality is, 73% of WordPress sites have no backup plan.
Think about that for a second. Three out of four site owners are one hack away from losing everything they’ve built.
So how do you actually back up your WordPress site?
Manual approach:
Your host might offer backups. Top hosting providers like Bluehost, Hostinger, and so on offer some type of backup plan with every plan you purchase.
But they delete those backups when you leave their hosting or after a certain number of months. Plus, if the server itself gets compromised, your backups go down with it.
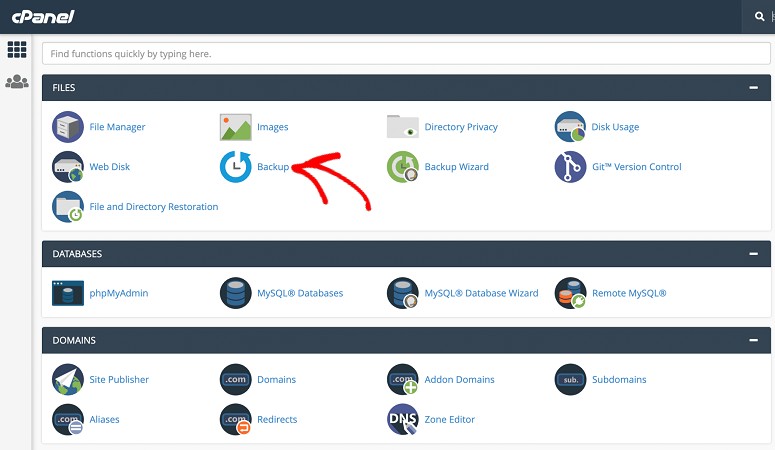
Remember, you need to understand how to operate your cPanel or SFTP if you want to use your host’s backup option. Check out this tutorial to see how to set up your site backup through cPanel or SFTP.
While having your backup with a hosting provider, never let it be your only solution. It’s like keeping your spare car key inside the car.
Tool solution: Duplicator (Free)
While manual backups through your hosts can be complicated to set up, using a plugin can automate the whole process.
For example, Duplicator solves the biggest backup security problem: recovery speed during an active attack.
When malware hits your site, you need to restore fast. Duplicator packages your entire WordPress installation into a single archive, including database, files, plugins, themes, uploads, everything.
One package means one-click restoration instead of piecing together scattered backup files during a crisis.
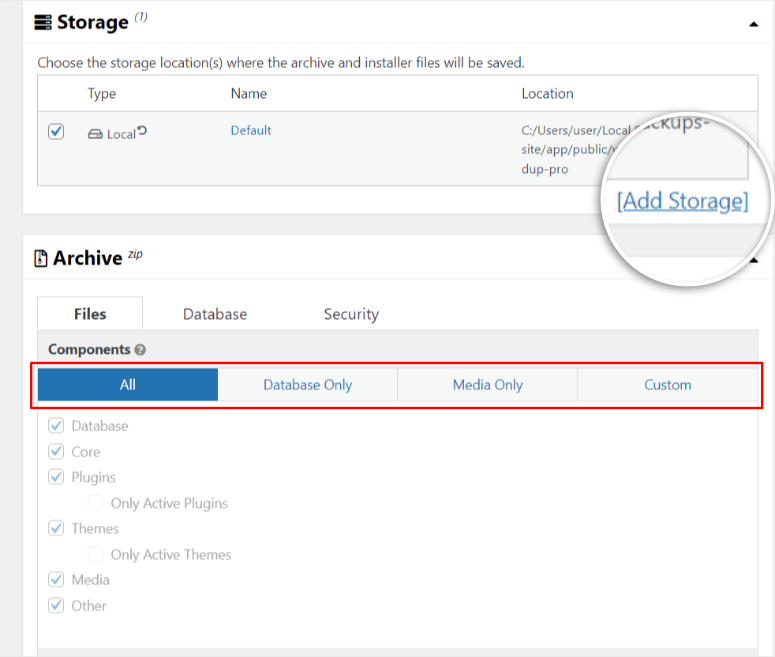
The scheduled backup feature runs automatically on your chosen timeline. You set it once. It backs up weekly or daily without you remembering to click anything.
This matters because manual backups fail when you forget during busy weeks.
Apart from that, you also get cloud storage integration sends your backups off-site immediately. You have options like Google Drive, Dropbox, Amazon S3, and more.
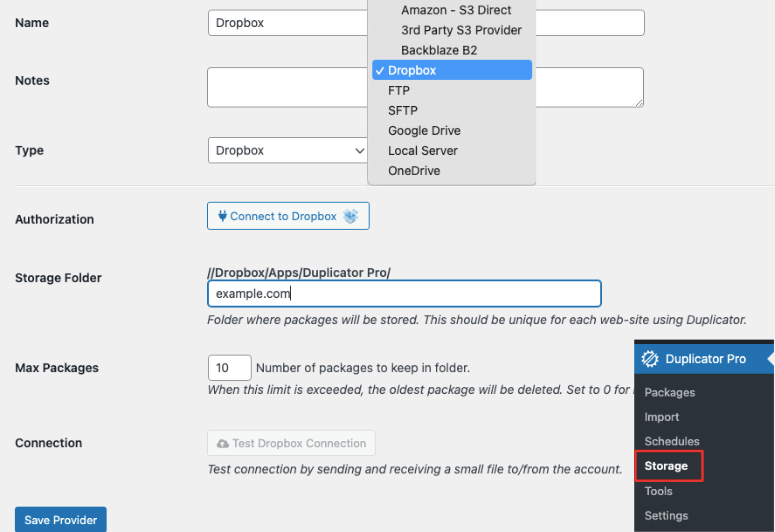
As a result, your backup never sits on the same server that attackers just compromised. Even if they delete everything on your hosting account, your backups survive in the cloud.
Most importantly, using Duplicator during hosting migration just makes sense.
If your host gets breached at the infrastructure level, you can move your entire site to new hosting in under an hour. You’re not trapped on compromised servers waiting for host cleanup.
Check out my Duplicator review here for more details. Also, look at this article to see how you can recover your site after a security breach. I walk you through 5 methods.
Alternatively, you can also use UpdraftPlus as your backup plugin.
UpdraftPlus offers a more visual interface with drag and drop backup scheduling. The restore wizard includes more hand-holding through each step, which some beginners prefer.
Both tools provide identical security benefits, so choose based on which interface feels more comfortable. Before you make your decision, compare Duplicator vs. UpdraftPlus vs. Solid Backups to see which is right for you.
Plus, you can also go through this list of the best backup plugins for even more options.
Verify your backups are working:
First, you get an email confirmation that lands in your inbox after each backup. This ensures you have a record of your backup every time. Plus, backup packages appear in your cloud storage with dates and timestamps.
High-Risk Sites Needing This Most:
News sites and content publishers face the biggest issues if they do not have site backups.
One successful attack can delete years of articles, author profiles, and multimedia content. That’s thousands of hours of work gone.
Unlike eCommerce where you might lose transaction data, WordPress news sites lose their entire business. The intellectual property that defines the publication.
Recovering this content from web archives or Google cache? Nearly impossible at scale.
☐ Enable Strong Authentication (2 minutes)
I often see site owners using “admin” as their username with “password123”, which is like leaving your house key under the doormat. Others use their names or business names which is just as risky.
Even a novice hacker will always try this combination before using any fancy bots to try to find your password.
But when these malicious people introduce bots to try to crack your site, even strong passwords may not help.
So how do you fully protect your site from password hacks?
Manual approach:
First and most obviously, you need to create strong passwords. More importantly, you need to use unique passwords for all your sites.
Just like I see many people using a simple username and password, I also see many site owners reusing the same password across sites because remembering 47 different passwords is impossible.
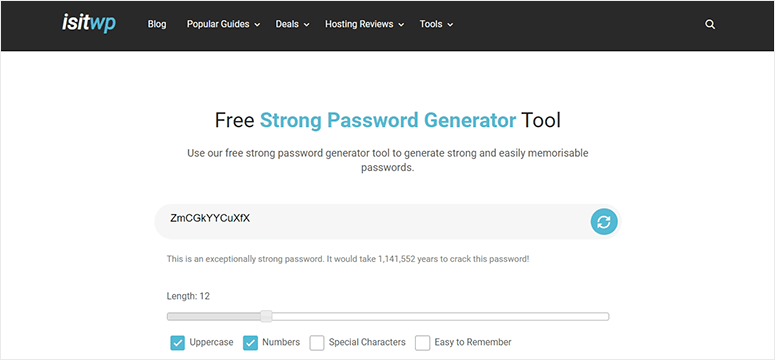
To help you create a strong password every time, you can use our free password generator.
You can see the length of the password. Then use checkboxes to tell the password generator to add uppercase, numbers, special characters, or make it easy to remember.
It is your choice.
As far as manually protecting your site with a strong password, this is the best solution. I suggest you save your passwords in a notepad so that they are off the grid and cannot be accessed remotely.
But this can be time-consuming and still present security concerns. That is why I prefer the tools approach.
Tool solution: Password Manager + 2FA Plugin
Password managers solve the “too many passwords” problem that leads to password reuse. As mentioned, when you reuse passwords, one breach on any site exposes all your accounts.
Password managers generate and store unique passwords for every site, so a breach somewhere else never affects your WordPress login.
LastPass offers a free tier with unlimited passwords on one device type. Plus, a more polished interface that many beginners find easy to use.
On the other hand, 1Password integrates beautifully if you’re in the Apple ecosystem, with features like Face ID and iCloud syncing. But requires a paid subscription with no free option.
Both generate random 16+ character passwords with letters, numbers, and symbols. Check out my list of tools to help you keep track of your passwords for more options.
So far, we have solved 2 of the biggest issues with passwords: creating strong passwords and remembering them. Now, let’s find out how to protect your site further if hackers bypass this.
And to do that, I recommend two-factor authentication.
This adds a second verification layer that attackers can’t bypass remotely.
Even if someone steals your password through a phishing email or data breach, they still can’t log in without the six-digit code from your phone.
WordPress 2FA plugins make this setup ridiculously simple. For example, most top two-factor authentication plugins connect to your phone with a QR code scan.
Your phone then generates time-based codes that change every 30 seconds. No codes ever transmit over the internet, so there’s nothing for attackers to intercept.
The backup recovery codes feature protects you if you lose your phone. These one-time-use codes stored in your password manager let you regain access and set up 2FA on a new device.
Without backup codes, losing your phone means paying a developer to manually disable 2FA in your database.
Here is a list of the best two-factor authentication plugins you can start with. Plus, here is how to set up a 2FA plugin in just a few steps.
What if you don’t want to use a WordPress authentication plugin?
In this case, you can use Google Authenticator and Authy, which both generate the six-digit codes WP 2FA needs.
Authy adds cloud backup of your codes across devices. Google Authenticator keeps everything local on one device for extra security.
What you achieve with 2 Factor Verification
First, you can quickly stop most brute force attacks immediately. Attackers can’t guess your phone. Even if they somehow steal your password, they still can’t log in.
As a result, account takeover becomes virtually impossible as most automated bot attacks give up and move to easier targets.
For a full look, here is a list of the best brute force plugins you can try.
High-Risk Sites Needing This Most:
Freelancer and portfolio websites operating as sole proprietorships face unique authentication risks.
This is because the WordPress admin contains client contracts, project files, payment information, confidential design mockups, and more.
A compromised account doesn’t just affect you. It exposes multiple clients’ confidential information at the same time.
One weak password can lead to breaching NDAs with several clients at once. Your professional reputation is destroyed. In the end, you are exposed to breach of contract lawsuits from multiple clients.
☐ Install Your Security Plugin (3 minutes)
Think of a security plugin as hiring a security guard who never sleeps.
See, WordPress doesn’t come with built-in attack protection. It’s secure software, but it has no idea when bots are hammering your login page or when malware gets uploaded.
A dedicated security plugin adds eyes and ears that WordPress simply doesn’t have by default.
It watches for threats around the clock. Blocks attacks before they touch your site. Alerts you to problems you’d never spot on your own.
Manual approach:
You could dive into server logs and write firewall rules. Analyze attack patterns manually. Track every file change yourself.
But honestly? Don’t. That’s way too technical for most people, and one wrong move locks you out of your own site.
Tool solution: Wordfence Security (Free)
Wordfence tackles the three security problems beginners struggle with most: spotting threats in real-time, scanning for vulnerabilities, and blocking attacks automatically.
The real-time firewall works like a bouncer at your site’s front door. When bots try adding bad code or cross-site scripting attacks, the firewall recognizes the malicious patterns and stops them cold.
In the end, the attacks never touch your database since your server never processes the bad code. They just vanish.
Daily malware scanning compares every file against WordPress.org’s official versions.
If attackers sneak in and modify your login code to create a backdoor, Wordfence catches it immediately.
The scanner checks against 4 million known malware signatures, hunting for suspicious code hiding in your plugins or theme files.
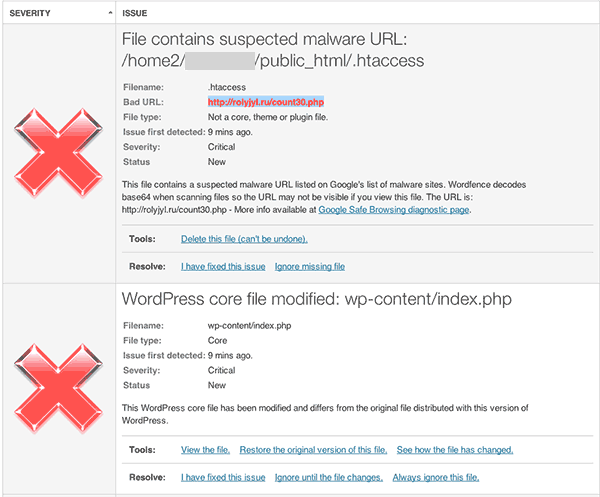
On top of that, failed login monitoring shows exactly who’s hammering your login page. You see their IP addresses, the usernames they’re testing, and how many attempts they’ve made.
After repeated failures, Wordfence automatically locks them out.
The setup wizard handles the technical decisions for you. Just click “accept recommended settings” and you’re protected. No need to understand what a web application firewall actually does.
Check out my detailed Wordfence review for more details.
Premium alternative: Sucuri Security
Sucuri offers a premium security platform that includes features Wordfence doesn’t match in its free version.
For starters, the cloud-based firewall blocks attacks before they even reach your server, reducing load and improving performance.
You get professional malware cleanup included if your site gets compromised. Best of all, the support team responds within hours, not days.
Sucuri also monitors major blacklists and alerts you immediately if Google or other services flag your site. Their security operations center provides 24/7 human monitoring, not just automated scans.
This firewall plugin is best for business sites where downtime costs real money and you need guaranteed expert cleanup if disaster strikes. Look at my Sucuri review for more details.
On top of that, check out my list for the best firewall security plugins for more options.
High-Risk Sites Needing This Most:
Membership sites and online course platforms depend on continuous uptime. Members pay monthly subscriptions, expecting 24/7 access to course content.
Real-time security monitoring prevents attacks that could take your site offline during peak learning hours.
When students can’t access course content they’ve paid for, chargebacks spike immediately. Membership cancellations follow.
One successful attack causing 24 hours of downtime can trigger hundreds of refund requests. Your payment processor sees the chargeback pattern. Your merchant account gets flagged.
Now, you can use our free uptime checker to always make sure your site is running smoothly.
Plus, here is a detailed list of the best security plugins that protect your site across different security levels, needs, and budgets.
☐ Verify Your Hosting Security (2 minutes)
One thing I have learned from my years as a WordPress expert is that your host is either your strongest security ally or your weakest link.
I noticed that 39% of compromised sites have outdated server software. That’s not your fault. That’s your host not doing their job.
Your hosting is the foundation of your entire security system. Everything you build sits on top of it. So how do you make sure your foundation is solid before adding the rest of your security layers?
The security foundation your host should provide:
The first thing you should make sure of is that your site is encrypted. This is a simple solution that you can achieve with an SSL (Secure Sockets Layer) certificate.
It protects data transmission between your site and visitors. If your site is SSL-protected, you will notice that the URL shifts from HTTP to HTTPS.
HTTPS encrypts everything traveling between your site and visitors. Without it, data moves in plain text that anyone can intercept.
Apart from that, Google won’t rank non-HTTPS sites well anymore. And modern browsers slap big red warning screens on sites without SSL, scaring visitors away before they even see your content.
Manual approach:
Request an SSL certificate from your host, then manually update your WordPress site URLs in the database.
After that, you’d need to set up .htaccess redirects forcing HTTP traffic to HTTPS. Then hunt down mixed content errors where images or scripts still load over HTTP, breaking your padlock icon.
The process involves editing database tables, modifying server files, and debugging why certain pages show security warnings.
One typo in your .htaccess file crashes your entire site. One missed URL in your database means broken links everywhere.
It’s technical, time-consuming, and honestly? Most beginners break something along the way.
The good news is that most hosting providers offer one-click SSL installation for free. Look for “SSL/TLS” or “Let’s Encrypt” in your hosting dashboard. Click “Enable” and wait 5 to 15 minutes for activation.
If your host doesn’t provide free SSL certificates, that’s a serious red flag about their infrastructure. Consider migrating to a host that includes SSL as standard.
Here is a list of the best hosts with free SSL certificates. On top of that, most hosting providers automatically install the SSL certificate.
Tool solution: Really Simple SSL (Free)
If a client hosting does not offer an SSL certificate, I turn to Really Simple SSL handles everything that manual setup makes complicated.
The encryption plugin automatically detects your SSL certificate the moment it runs. One click on the big “Activate SSL” button and you’re done.
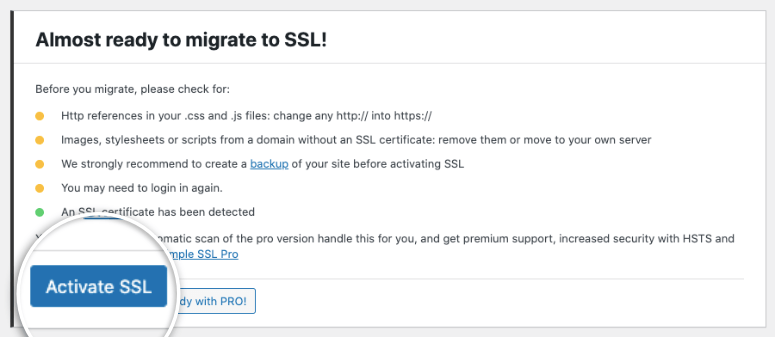
Really Simple SSL handles everything behind the scenes. It changes your WordPress URLs from http:// to https:// safely in your database.
Manual database edits that can easily break your entire site with one typo? Really Simple SSL does it correctly every time.
Plus, it also automatically sets up redirects to force all visitors to the HTTPS version. This way, search engines see the HTTPS version, and users never hit the insecure version.
Check out my Really Simple SSL review to see how it works. On top of that, here is a step by step guide on how to manually or use a plugin to set up your SSL certificates.
High-Risk Sites Needing This Most:
Real estate and property listing websites require hosting with excellent security.
You handle sensitive client data such as home addresses and financial information, showing what buyers can afford.
One of the biggest risks is that you show schedules revealing when properties are vacant. So, weak hosting security exposes when properties are empty. That’s not just a data breach. That’s creating physical security risks for homeowners.
Apart from sourcing user information and financial records, attackers targeting real estate sites often seek addresses of high-value properties for burglary planning.
Robust hosting security isn’t optional. It’s protecting your clients’ physical safety. And it all starts with where your site servers are.
You can go through this comparison list of secure and top-performing hosting providers to start with.
☐ Lock Down User Access (3 minutes)
Here’s a scary stat: 55% of hacked sites contain fake admin accounts created by attackers.
These aren’t obvious usernames like “hacker123.” They’re accounts named like real users or roles like “john_smith” or “support_team” that sit dormant for months.
Attackers create them during the initial breach, then come back later to use them. By then, you’ve forgotten about the attack and assume everything’s fine.
Locking down who can access your site stops this before it starts.
Manual approach:
The manual approach can be time-consuming, but it is very effective in identifying users who may have malicious intent.
All you have to do is go to Users » All Users, then check every account. Question every username you don’t immediately recognize.
But manual checking only works if you remember to do it. Most people forget until after the breach.
So how do you make sure you “remember” everyone?
First, delete any user named “admin.” Instead, change it to your real name or business name. Attackers specifically target the default “admin” username because it’s guaranteed to exist on lazy installations.
Next, remove old accounts. This includes former contractors or employees with whom you are no longer working with.
If you have many users on your site, it becomes impossible to remember them all.
So instead of focusing on the “who,” focus on the “role.”
This ensures that every user has the correct access level. Your content writer doesn’t need Administrator access. Your virtual assistant doesn’t need Editor privileges to schedule posts.
Use this approach to set up roles:
- Administrator means complete control. Only you, the site owner, should have this. Maybe your lead developer if you’re running a business.
- Editor handles all content management. They can publish, edit, and delete any posts or pages. Good for content managers who need full content control.
- Author creates and publishes their own content only. Perfect for regular writers on your blog.
- Contributor writes content but can’t publish without approval. Use this for guest writers.
- Subscriber just reads content. They can log in and comment, but nothing else. Most members should be subscribers.
Tool solution: WP Activity Log (Free)
WP Activity Log solves the “who did what” problem that makes breach investigations impossible.
The activity monitoring feature records every login, logout, and action taken by every user. When something goes wrong, you see exactly which account made the change and when.
This matters because attackers often use compromised legitimate accounts rather than creating obvious “hacker123” usernames.
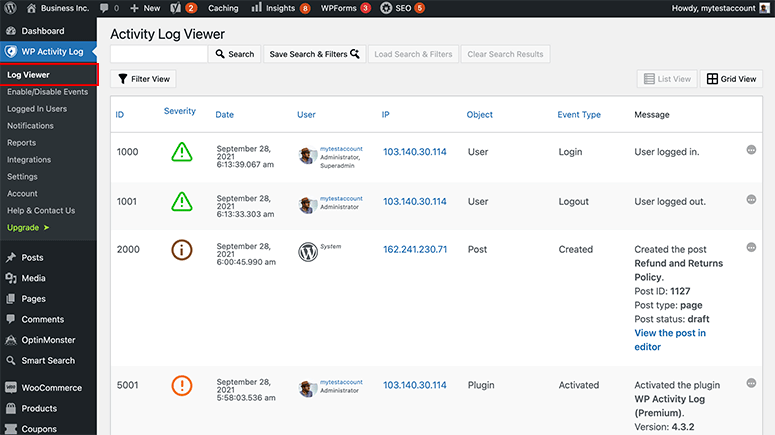
Apart from that, new admin account alerts notify you immediately when administrator accounts are created. This alert catches them in real-time, not three months later during your next manual audit.
Login time tracking shows unusual patterns like your account logging in from Russia at 3 AM when you’re asleep in California.
Geographic anomalies reveal compromised credentials before attackers do real damage.
Session management displays all active login sessions. You can see if your account is logged in from multiple locations simultaneously and kill suspicious sessions instantly.
See how to use WP Activity Log to track user activity for an added layer of protection. Plus, here are more tools to track visitor traffic to help you spot any abnormalities.
High-Risk Sites Needing This Most:
Community forums and discussion boards face extreme user management challenges because they allow public registration by design.
Attackers create seemingly legitimate member accounts. They slowly build reputation through normal participation over weeks or months.
Then they find ways to boost their account from a regular member to a full administrator.
Once inside, they access private messages between all members and expose email addresses for spam campaigns. Worst of all, they inject malware affecting every forum visitor.
The slow-build attack is nearly impossible to prevent without activity monitoring. Regular members don’t trigger suspicion until it’s too late.
☐ Clean Up Your Plugins (4 minutes)
96% of WordPress security holes come from plugins, not WordPress itself.
As mentioned, WordPress core is rock solid. The WordPress team fixes vulnerabilities within hours of discovery. In all of 2024, only 7 core vulnerabilities were found.
But your plugins? That’s where attackers focus. Every plugin you install adds code from different developers with varying security standards.
Some plugins get abandoned, others have sloppy code, and a few contain hidden backdoors. Your plugin collection is your biggest security risk.
Manual approach:
Go to Plugins » Installed Plugins and count them. For me, the average WordPress site runs 20+ plugins. So the first thing you need to look at is the total number of plugins you have.
Next, sort your plugins into three categories.
- Essential plugins handle security, backups, SEO, and core functionality you can’t operate without.
- Nice-to-have plugins add convenience but aren’t critical.
- Unused plugins just sit there collecting dust.
After sorting your plugins into the categories above, delete anything unused in 3 months. Not deactivate. Delete completely.
Inactive plugins can still be exploited. The code sits in your directory, where attackers can access vulnerable files directly, even when deactivated.
Next, go to your “Nice to have” list and check for the following red flags.
- Last updated within 6 months means active maintenance. Over a year old? Security nightmare waiting to happen.
- WordPress compatibility matters. Incompatible plugins often have unpatched vulnerabilities.
- User reviews should show 4+ stars with recent positive feedback. Scroll through, checking for security complaints.
- An installation count above 10,000 means community testing. More users means security issues get reported and fixed faster.
- Developer responsiveness shows someone’s home. Check if they answer support questions. Abandoned plugins are ticking time bombs.
If you spot any of these red flags, replace them immediately. On top of that, enable auto-updates for trusted essentials.
Keep manual updates for page builders since auto-updates in this case can break your site. Most importantly, remember to update your plugins during low-traffic hours to avoid any downtime.
Theme security works the same way as plugin security.
This is because abandoned themes create the same vulnerabilities as abandoned plugins.
In the same way, delete old unused themes completely and keep your active theme updated. Default WordPress themes can stay since WordPress.org maintains them.
Remember, verify your active theme has been updated within the last 6 months. Here is a list of modern themes with great user experience and security features to get you started.
Tool solution: Your current security plugin should handle this automatically.
Now, the beauty of most top security plugins is that they are multipurpose and handle all the basics like securing your plugins effectively.
For example, Wordfence scans your plugins against a constantly updated vulnerability database. When it finds problems, you get specific alerts with severity ratings.
Not just vague “update available” notices, but clear warnings like “this version has an SQL injection vulnerability actively being exploited.”
Sucuri‘s scanner works similarly, checking your plugins against known threats and highlighting which ones need immediate attention.
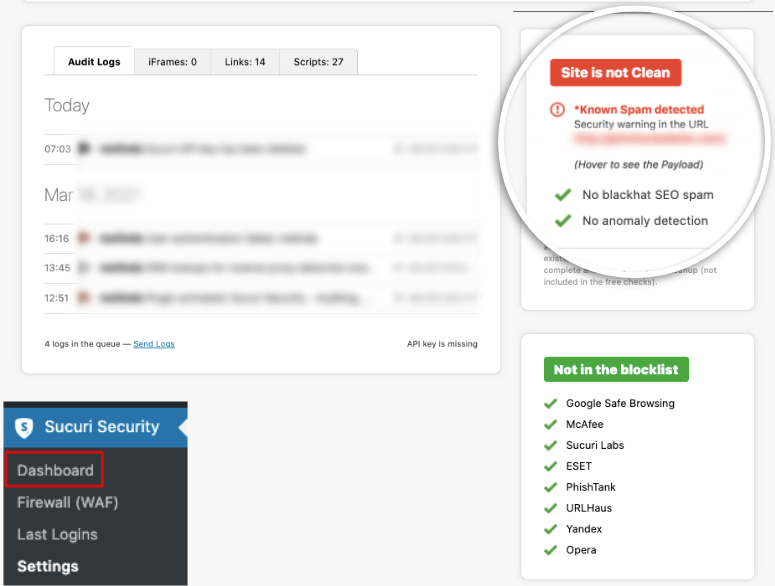
iThemes Security, now Solid Security, also monitors plugin vulnerabilities and can block specific plugin files from executing if they’re compromised.
On the other hand, All-in-One WP Security takes a slightly different approach, letting you disable plugin and theme file editing directly from the WordPress dashboard.
This prevents attackers from modifying plugin code even if they compromise an admin account.
As you can see, you don’t need a separate plugin just to monitor plugins. Your main security tool already watches everything.
It checks for outdated versions, known security holes, and suspicious code modifications. You can go through this list of the best general-purpose security plugins to see which one is right for you.
High-Risk Sites Needing This Most:
Photography and creative portfolio sites typically install numerous gallery, slideshow, and image optimization plugins to showcase work beautifully.
Each specialized visual plugin adds potential vulnerabilities. Attackers specifically target photography sites to steal high-resolution images for unauthorized commercial use.
One compromised gallery plugin can expose your entire portfolio. Competitors can then download and sell your digital work before you discover the breach.
☐ Limit Login Attempts and Device Access (3 minutes)
As mentioned, WordPress allows unlimited login attempts by default. Attackers can hammer your login page with thousands of password combinations without ever getting blocked.
Your security plugin, like Wordfence, already handles basic blocking, but adding dedicated login limiting creates an extra security layer.
Plus, restricting how many devices can access each account prevents credential sharing that creates security gaps you’d never notice.
This step closes the “unlimited tries” loophole that makes brute force attacks possible.
Manual approach:
Write custom code in your functions.php file, tracking failed login attempts by IP address.
Next, build a database table storing attempt counts and create logic that temporarily blocks IPs after reaching your threshold.
Then manually track which devices each user logs in from and store device fingerprints, comparing new login attempts against known devices. Then, finally, block access from unrecognized devices.
Sounds complicated, right?
This requires understanding PHP sessions, database management, and device identification methods. One coding error breaks your login system completely, locking everyone out, including you.
So let me show you an easier approach.
Tool solution: Sucuri Security + WPCode
Sucuri (free version) includes login attempt limiting that blocks IP addresses after repeated failures. Set your threshold – typically 3 to 5 failed attempts within a specific time window.
Once that limit hits, Sucuri blocks that IP from accessing your login page entirely.
The plugin logs every failed attempt, showing usernames attackers tried, their IP addresses, and exact timestamps.
You see attack patterns emerge – some come from single IPs testing common passwords, others use rotating proxy networks trying targeted credentials.
Sucuri’s blocking happens at the plugin level before WordPress processes the login request, saving server resources. Failed attempts from blocked IPs consume almost zero processing power.
Here is my step-by-step tutorial on how to limit login attempts.
On the other hand, use WPCode for device restrictions.
It lets you add custom code snippets safely without editing theme files.
For restricting users to one device, WPCode provides a code snippet library where you can add device restriction logic that tracks login sessions.
The snippet monitors user sessions and automatically logs out previous sessions when someone logs in from a new device.
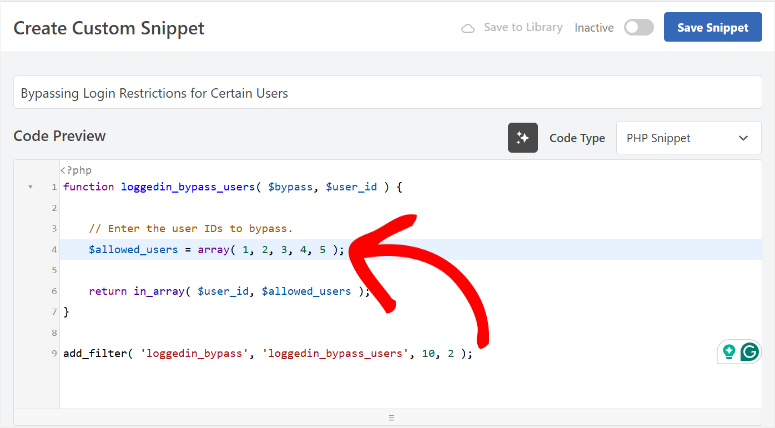
The best part is that you’re not writing code from scratch – you’re using tested snippets that WPCode manages safely.
If the code has issues, disable it through WPCode’s dashboard without breaking your site. No FTP access needed. No crashed sites from typos in functions.php.
Check out my detailed tutorial on how to limit login devices in WordPress. You can also go through my WPCode review to see all it can do.
High-Risk Sites Needing This Most:
Online course platforms and digital product sites lose massive revenue when customers share login credentials.
One course purchase shared across a study group means 9 lost sales. In this case, device limits per account stop this revenue leakage while improving security.
Educational platforms also face legal compliance issues when credential sharing occurs.
If your terms of service prohibit account sharing but you don’t enforce it technically, you’re relying entirely on the honor system.
Again, device restrictions provide the technical enforcement that terms of service can’t.
☐ Secure WordPress Core Files (4 minutes)
Since WordPress itself is secure because of all the patches they run, the real risk is running outdated versions.
Remember, every security patch WordPress releases is public information.
Like you, attackers read the patch notes, reverse-engineer the vulnerability, then scan the internet for sites still running the old version.
As a result, you’re not just missing a security update. You’re advertising a known weakness that hackers actively target.
To help with this, keep WordPress current to close these documented security holes before attackers find your site.
Let me show you how.
Manual approach:
Go to WordPress and select Dashboard » Updates. Then click through, review available patches, and update WordPress core. The process takes just a few minutes when updates are available.
The challenge? Maintaining weekly discipline over months and years.
WordPress does email you when new updates drop, but those notifications get buried in your inbox alongside newsletters, client emails, and spam.
You see “WordPress 6.4.3 now available” and think “I’ll handle that tonight.” Then you forget.
You can support the email alerts by setting weekly calendar reminders. Schedule 15 minutes every Monday morning specifically for WordPress maintenance. Treat it like any other recurring appointment.
Always remember to maintain perfect discipline if you want to update your core files manually.
Tool solution: Easy Updates Manager (Free)
Easy Updates Manager solves the “forgetting to update” problem that leaves sites vulnerable for months.
First, it comes with an automatic minor updates feature, which installs security patches immediately after release.
For example, minor updates like WordPress 6.4.1 to 6.4.2 contain only security fixes and bug patches, which Easy Updates Manager handles automatically without your input.
But for major WordPress updates, you will use the Manual Major Update Approval feature instead. It lets you control big feature updates yourself, reducing the risk of breaking something.
Major updates like WordPress 6.4 to 6.5 introduce new features that might conflict with your theme or plugins.
So, with this feature, you can test the new WordPress update on a staging site first before you move it to your main site.
Remember to use a reliable staging plugin or your host’s staging environment so that it replicates your original site properly.
High-Risk Sites Needing This Most:
Restaurant and hospitality websites with online reservation systems face critical security needs.
Breaches reveal exactly when VIP clients or celebrities plan to dine, creating privacy violations and genuine physical danger.
Paparazzi stake out restaurants using leaked reservation data. Stalkers track celebrity movements and dining patterns. Thieves target burglaries when high-profile individuals are confirmed to be dining out.
Beyond names and times, leaks expose dietary restrictions, health conditions, phone numbers, credit card details for no-show charges, and private celebration notes.
☐ Clean and Protect Your Database (2 minutes)
Your database is the vault where everything lives.
It contains every post you’ve written, every user account and password hash, every plugin setting and configuration, every comment, image metadata, and custom field.
Hackers target databases because one successful breach gives them everything at once. They don’t need to hunt through individual files. The database hands them your entire site on a platter.
Plus, database attacks are often invisible. Your site looks normal, and pages load fine. But attackers are quietly extracting user data or injecting malicious content into posts.
Manual approach:
You first must access your site’s database directly through your hosting control panel. This gives you an opportunity to edit database tables manually and run cleanup commands yourself.
On top of this, you can navigate through phpMyAdmin and hunt for bloated tables. Here you can write SQL queries to delete spam comments or optimize table structures.
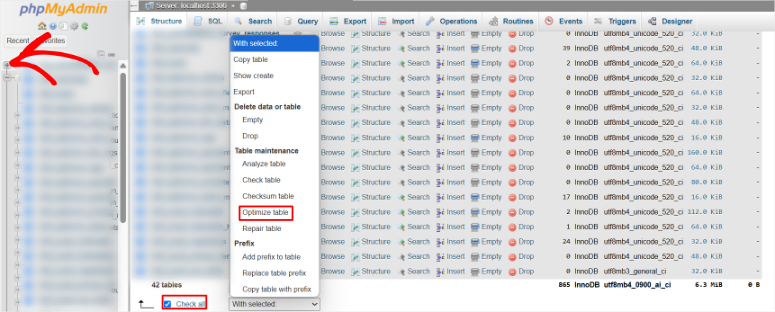
The problem? Databases are unforgiving!
There’s no undo button. One wrong command wipes out all your posts. A mistyped table name deletes every user account. A single typo erases months of work permanently.
Plus, working directly with databases requires understanding complex technical concepts. Most beginners feel lost the moment they open the database interface.
Because all you see is rows of cryptic data with no clear explanation of what anything does.
It’s risky. So, only use the manual approach if you have developer experience. If you do, follow my detailed guide on how to clean your WordPress database for a full tutorial.
I also show you how to delete unused files in your database if you notice any that create a security concern.
Tool solution: WP-Optimize
WP-Optimize solves the “database bloat” problem that both slows your site and creates security vulnerabilities.
Plus, the spam comment removal feature deletes thousands of spam comments cluttering your database. Spam comments create weak spots in your database that hackers exploit to sneak in malicious code.
This optimization plugin also helps with post revision cleaning, removing old draft versions WordPress saves automatically.
Every time you save a draft, WordPress creates a new database entry. After a year, you might have 50 revisions of a single post. The plugin keeps your 3 most recent revisions and deletes the rest.
Best of all, WP-Optimize is easy to use, and most database optimizations are enabled with a checkbox.
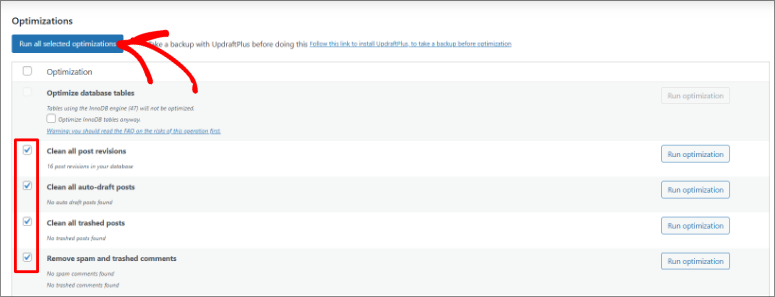
In a nutshell, database optimization tidies up and compresses your data. Your site loads faster and uses less storage space.
Apart from WP-Optimize, here are other database tools to clean and optimize your site.
High-Risk Sites Needing This Most:
Job boards and career platforms maintain databases filled with thousands of resumes.
This information includes full names, addresses, phone numbers, employment histories, salary expectations, and more.
This concentrated personal information makes job sites prime targets for identity theft operations. One database breach exposes hundreds of job seekers’ complete professional histories.
Criminals use this data for sophisticated phishing attacks. They impersonate recruiters to steal banking information for “direct deposit setup.”
Resume data sells for premium prices on dark web markets because it’s so complete and current.
Advanced Protection Layer (8 Minutes)
You’re now more secure than 80% of WordPress sites. You can actually stop your WordPress security optimization here and rest assured that you are protected. But you can still do more!
These advanced measures add monitoring and protection against sophisticated attacks. Think of this as upgrading from a basic alarm to a comprehensive security system.
☐ Add a Web Application Firewall (3 minutes)
A Web Application Firewall sits between your website and everyone trying to visit it. Think of it as a bouncer at a nightclub entrance.
Every request trying to reach your site gets checked first. Legitimate visitors pass through instantly, while malicious traffic gets blocked before it ever touches your server.
This matters because attacks consume your server resources even when they fail. Without a firewall, your hosting server wastes energy processing thousands of malicious requests daily.
In the end, your site slows down, and real visitors experience lag.
With a WAF, attack traffic never reaches your server at all. Your hosting resources serve real visitors only.
Manual approach:
Log in to your hosting control panel and navigate to the firewall settings. Here, you need to write rules that define which traffic patterns to block.
After this, create lists of IP addresses you want to deny access to and update these lists as new threats emerge.
You’ll need to specify exactly which types of requests get blocked while ensuring legitimate visitors still get through.
Always test each rule carefully because blocking the wrong pattern can prevent real customers from accessing your site. One wrong configuration and you might lock yourself out completely.
Remember, managing this manually means checking logs daily, identifying new attack sources, and adding them to your block list one by one. It never stops.
Tool solution: Cloudflare (Free)
Cloudflare stops attacks before they reach your website, preventing crashes during traffic floods.
The cloud-based filtering means attack traffic never reaches your hosting server. Even DDoS attacks, throwing 100,000 requests per second at your site, get absorbed by Cloudflare’s network.
As a result, your server only receives legitimate visitor traffic.
Plus, the global CDN network caches your static content across 300+ data centers worldwide. This makes your site faster while blocking attacks at the same time.
Cloudflare offers another way to get an automatic SSL certificate, other than the ones we have discussed above. This gives you a backup SSL certificate even if your host’s certificate expires.
Your site stays encrypted during certificate renewal periods.
The best part is that you can easily set up the security rule engine to block malicious traffic patterns automatically.
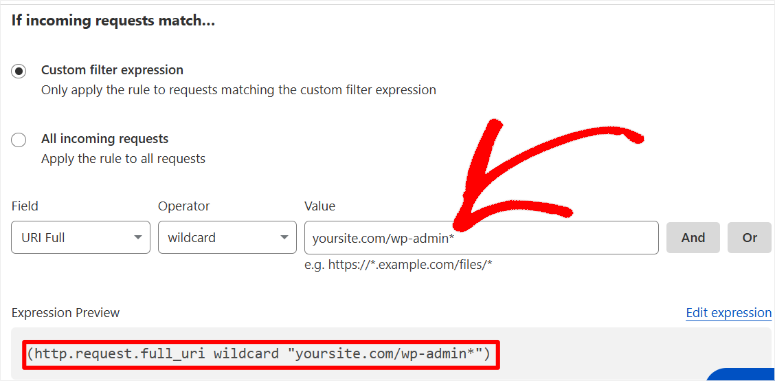
Cloudflare sees billions of requests daily across millions of sites. So, when new attack patterns emerge, their network recognizes and blocks them before attackers reach your site.
Here is a guide to help you set up Cloudflare and optimize your site for security and performance. On top of that, here are other firewall plugins that you can also use instead of Cloudflare.
High-Risk Sites Needing This Most:
SaaS and web application platforms built on WordPress often face coordinated attacks attempting to exploit API endpoints and user authentication systems.
Without a firewall, attackers flood your site with millions of login attempts. They test millions of stolen username and password combinations to hijack user accounts.
These attacks consume server resources even when unsuccessful. Your site slows down, and real users experience timeouts and errors.
Performance struggles and drives real users away during critical business hours. As a result, your paying customers can’t access their accounts, and support tickets flood in.
☐ Set Up Malware Scanning (4 minutes)
We have already talked about using a malware scanner above.
But since we are now talking about advanced WordPress security, it is important to realize that one scanner or scan does not catch everything.
Different scanning tools look for different threats. Wordfence might miss something Sucuri catches. Google’s scanner spots issues that slip past both.
Think of it like getting a second medical opinion. Your first doctor might be excellent, but another perspective reveals things the first missed. Malware scanning works the same way.
Using multiple free or premium scanners together creates layers of detection. What one misses, another finds.
Manual approach:
Download every file from your site via FTP. Then open them in text editors, and scan the thousands of lines of code for suspicious patterns.
Your site contains thousands of files, and malware hides itself as real code. One file review takes 10 minutes, turning manual malware detection into a full-time job that still misses most threats.
As you can see, this is not practical at all, no matter how experienced you are. So, for this, I always recommend scanning tools.
To ensure you find a good combination of malware scans, I will provide a short list of manual and premium malware scanning options for you.
Tool solution: Free and Premium Malware Scanner and How to Combine Them
1. IsItWP Free Security Scanner – 100% Free
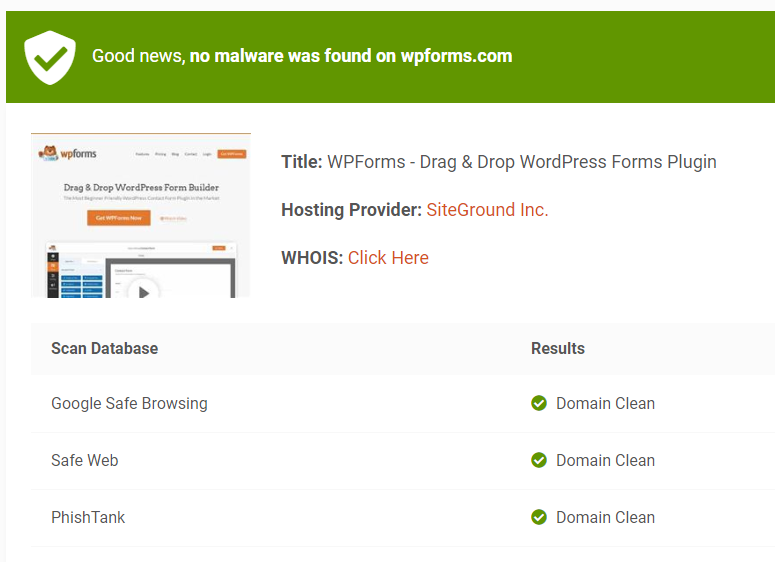
IsItWP’s free security scanner checks your entire WordPress site for malware, vulnerabilities, and security issues in seconds.
All you have to do is enter your URL and get instant results showing malware detection, blacklist status, outdated software, and security misconfigurations.
There is no plugin installation required. The scanner runs externally, so it won’t slow your site down while checking thousands of files for threats.
2. Google Search Console – 100% Free
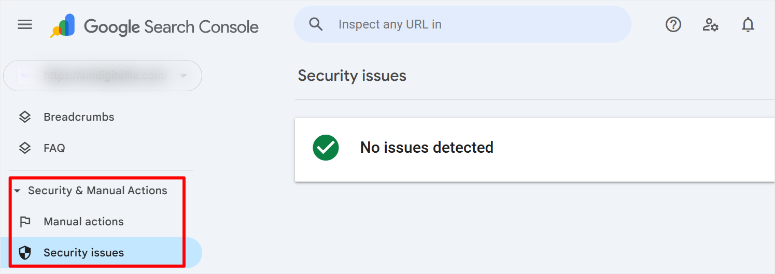
Google Search Console monitors your site continuously as part of Google’s crawling process; you do not have to set up anything.
When Google detects malware, phishing attempts, or hacked content, you receive immediate email alerts. The Security Issues report shows exactly what Google found and which pages are affected.
3. Sucuri Security – Free, with Premium Version
Sucuri‘s free plugin provides basic security hardening and activity monitoring, helping you track changes on your site and implement recommended security settings.
On the other hand, the premium SiteCheck scanner adds cloud-based malware detection that runs externally without consuming your server resources.
You also get professional human cleanup if your site gets infected. Premium includes a website firewall that blocks attacks before they reach your server and priority support with security experts available 24/7.
Check out my updated Sucuri review here.
2. Wordfence Security – Free, with Premium Version
Wordfence Free scans your site daily for malware by comparing files against official WordPress versions, catching unauthorized modifications and known malware signatures.
While the premium upgrades give you real-time threat intelligence that updates within minutes of new threats being discovered, instead of waiting 30 days.
You also get country blocking to stop traffic from high-risk regions, two-factor authentication for all user accounts, and advanced firewall rules that adapt to emerging attack patterns.
Check out my latest Wordfence for more details.
3. MalCare– Free, with Premium Version
MalCare‘s free version offers basic security scanning that checks your site for common vulnerabilities and configuration issues.
The premium provides off-site malware scanning that happens on MalCare’s servers rather than yours, preventing any performance impact during scans.
You get one-click automated malware removal that cleans infected files without breaking functionality. Plus, database scanning that catches malicious content injected into posts and comments.
Premium includes staging site environments for safely testing updates before pushing them live.
These 5 malware scanners work best in spotting any malware in different ways. But as mentioned, you need to combine them to give you a better chance of nothing slipping through the cracks.
How to Combine Malware Scanner
Combining Free Scanning Tools
First, run IsItWP’s external scan weekly to catch threats from outside your network. Remember, malware often hides from internal scanners but reveals itself to external checks.
At the same time, Google Search Console monitors continuously in the background. Set it up so that it alerts you when Google detects issues during crawling.
Finally, use Wordfence Free to provide daily internal file scanning, comparing your WordPress files against official versions. This three-layer approach catches threats from multiple angles while costing nothing.
Combining Premium Scanning Tools
Combine Wordfence Premium with Sucuri’s cloud scanner for business-grade protection. Wordfence provides real-time threat intelligence updates within minutes of discovery.
Plus, internal malware scanning with immediate alerts.
On the other hand, Sucuri adds cloud-based external scanning that catches threats Wordfence misses. You also get professional human cleanup if malware breaks through.
Alternatively, pair MalCare with Wordfence Premium for off-site scanning that doesn’t consume server resources.
Either combination gives you internal monitoring, external verification, automated cleanup, and real-time threat updates.
Here is a list of the best malware scanners you can use for WordPress.
High-Risk Sites Needing This Most:
Non-profit and charity websites accepting online donations face malware attacks designed to redirect donation payments to attacker-controlled accounts.
These attacks quietly change payment pages so donations go to criminal accounts instead of your charity. Everything looks normal to donors. They get confirmation emails, thinking their money helped your cause.
Months later, they discover their $10,000 donation, expecting a tax deduction, never reached your organization. It went to criminals.
In the end, charity regulators investigate when financial records don’t match and your non-profit status gets questioned.
You face potential loss of tax-exempt status. Donors lose trust permanently, even though you were the victim.
☐ Add Advanced Login Protection (2 minutes)
We have already talked about how to create strong passwords and then store them in your password manager. We have also looked at two-factor authentication, which protects your login with codes from your phone.
This combination blocks 99% of login attacks because bots can’t guess your password. Even if they somehow steal it, they can’t access your phone for the second authentication code.
But here’s the thing: attackers still know where to find your login page. Every WordPress site uses /wp-admin by default. So all bots have to do is hammer this URL constantly across millions of sites.
Now, let’s look at one more simple layer that hides your login page completely, making it invisible to automated attacks.
Manual approach:
Open your site’s functions.php file and write custom code that redirects the default login URL to something that hackers can’t guess.
So, instead of “Yoursite.com/wp-admin” it is something like “Yoursite.com/random-charecters” or “yoursite.com/backend-access.”
Then, add rules that track login attempts by IP address. After this, build your own system for blocking repeated failures.
The problem? One typo in functions.php crashes your entire site with a white screen of death. Your site goes down. You can’t access the admin area to fix it.
You’d need to connect via FTP and manually edit or delete the broken code to get your site back online.
Plus, you’d need to understand PHP syntax, WordPress hooks, and redirect logic. Most beginners don’t know where functions.php lives or how to edit it safely.
Tool solution: WPS Hide Login (Free)
WPS Hide Login helps you change your login page URL from the same predictable login URL that bots attack constantly to a custom one.
You see, the custom login URL feature changes your login page from yoursite.com/wp-admin to whatever you choose – maybe yoursite.com/secure-access or yoursite.com/backend-2024.
The plugin creates a completely custom login path that only you know. Automated attacks can’t find what they can’t see.
Your login page becomes invisible to the bots scanning millions of sites for the default wp-admin URL.
Bots still hammer /wp-admin looking for your login page, but now they just hit a 404 error and move on to easier targets.
Critical reminder: Save your new login URL in your password manager immediately. If you forget it, you’ll need FTP access to disable the plugin and regain access.
Beyond hiding your login page, you can enhance user login security further with specialized login and registration plugins that add features like social login, custom registration forms, and advanced user management.
Check out my guide to the best user login and registration WordPress plugins for more ways to secure and customize your login experience.
High-Risk Sites Needing This Most:
Blogger and influencer websites with large social media followings attract targeted attacks from competitors and trolls who know the site owner’s identity.
Custom login URLs prevent harassment campaigns. Angry followers or jealous competitors attempt to brute force login credentials they’ve gathered from social media profiles.
Remember, public figures often face coordinated attacks during controversies. When you post something controversial, people can try to break into your WordPress admin.
Hiding wp-admin removes the easiest attack path during these crisis moments, ensuring attackers can’t find your login page to attack it.
Well done! Your advanced and basic protection is now active.
Now let’s look at some common mistakes to avoid while working on WordPress security.
Common Beginner Mistakes (And How to Avoid Them)
“I’ll deal with security later”
- Sites get attacked within hours of going live. Attackers scan for new WordPress installations constantly.
- Solution: Implement basics during initial setup. This 40-minute checklist during site launch prevents months of problems.
Using weak passwords everywhere
- Password reuse leads to many interconnected security concerns. One breach at any site exposes all your accounts using that password.
- Solution: Password manager from day one. Bitwarden or LastPass. Generate unique passwords for everything.
Installing too many plugins
- Each plugin is a potential vulnerability. The average hacked site runs 25+ plugins, including several abandoned ones.
- Solution: Monthly plugin audit. Delete anything unused in 3 months. Quality over quantity.
Ignoring update notifications
- 33% of hacked sites had available security updates sitting uninstalled. Attackers specifically target known vulnerabilities.
- Solution: Enable auto-updates for trusted plugins. Manual updates for complex functionality only.
Not testing backups
- 40% of backups fail to restore when needed. Untested backups provide false confidence during emergencies.
- Solution: Monthly backup restoration test. Download a backup package and verify it opens.
Sharing admin login credentials
- Can’t track who made changes or who got compromised. Multiple people using one admin account hides breaches.
- Solution: Individual accounts with appropriate roles. Editor for content managers, not Administrator.
Using nulled or pirated plugins
- Premium plugins cracked and distributed for free often contain hidden malware backdoors built into the code.
- Solution: Use official plugins only. Pay for premium if needed. Free alternatives exist for most functionality.
Panicking during incidents
- Hasty decisions make problems worse. Deleting files randomly or changing settings frantically creates more damage.
- Solution: Follow documented response procedures. Take the site offline if needed and restore from clean backup. Get professional help.
Congratulations! That marks the end of our WordPress security checklist. If anything is unclear, check out the commonly asked questions below.
FAQ: WordPress Security Checklist
How long does WordPress security really take?
If you are going to do both the basic and advanced WordPress security processes in one sitting, it will take you 40 minutes using my detailed checklist. Most security runs automatically after initial setup, so ongoing maintenance will take significantly less time.
Do I need to pay for security plugins?
Free versions handle 95% of security needs for personal sites. My recommendation is to use the free versions of Wordfence, Duplicator, and Cloudflare to provide solid protection. Upgrade to premium when your site generates revenue or handles customer data. In this case, real-time threat updates and priority support become valuable for business sites.
What if my site is already hacked?
Don’t panic. Hasty decisions make problems worse. First, take your site offline using maintenance mode. Here are some maintenance mode plugins you can use. This protects visitors and prevents further damage.
Second, scan with Wordfence and external scanners like Sucuri SiteCheck to identify the extent of compromise.
Third, restore from a clean backup created before infection. Your Duplicator backups make this one-click easy.
Fourth, implement this entire checklist to prevent reinfection. Remember, attackers often leave backdoors allowing easy re-entry.
How do I know if my security is working?
Use a malware scanner to check your site and make sure it shows zero malware found in weekly scans. Also, check for things like 100% successful backup completion with email confirmations arriving for every scheduled backup.
Make sure you have few failed login attempts after you set up a custom login URL and 2FA, which reduces attacks by 90%+.
Most importantly, you should receive no Google security warnings when searching your site. At the same time, ensure Google Search Console shows no manual penalties.
Which free security plugin is best for beginners?
Wordfence free version has over 4 million installations. A huge community support means finding answers to problems takes minutes not hours. It also comes with great documentation for learning security concepts.
The setup wizard helps you quickly install it and make good WordPress security decisions automatically. You don’t need technical knowledge to get solid protection.
All-in-One Security provides a simpler interface if Wordfence feels overwhelming. Both offer complete free protection.
Can too much security slow down my site?
Quality security tools like Wordfence and Cloudflare often improve speed. Cloudflare’s CDN makes your site faster while adding security.
Only issue: Installing multiple security plugins duplicates features and conflicts, reducing your performance.
The solution is picking one comprehensive security plugin that fits your needs and sticking to it.
How often should I update WordPress?
For minor updates, you can automatically update within hours of release. But even though they can come as minor updates, security patches need immediate installation.
On the other hand, major updates should be done within 1 to 2 weeks after release for most sites. It is important to test on staging sites first if you have complex custom functionality.
- Plugins: Weekly check for available updates. Enable auto-updates for trusted essential plugins.
- Theme: Monthly check unless you’re actively developing. Themes change less frequently than plugins.
Regular updates prevent 33% of successful hacks because most attacks exploit old known vulnerabilities, not zero-day exploits.
Final Verdict: How Important Is WordPress Security for Your Business?
WordPress security isn’t optional anymore. It’s the foundation everything else builds on.
And with this detailed security checklist, you’ve just implemented protection that 80% of WordPress sites don’t have.
You now have automated backups safeguarding your work and real-time monitoring catching threats before they spread.
On top of that, you have hardened login systems blocking 99% of attacks, which work hand in hand with the professional-grade firewalls you have set up..
The 40 minutes you invested today prevents the $2,000 cleanup bills, the week of downtime, the lost customer trust, and the months recovering search rankings after breaches.
You’ve built systems that protect your investment while you focus on growth.
Now that’s smart business.
Want to make even smarter business decisions about security?
- Start with our complete WordPress security guide for deeper understanding of threats and protection strategies beyond this checklist.
- Compare backup solutions like Duplicator vs UpdraftPlus vs BackupBuddy to find the perfect backup tool matching your site’s specific needs and budget.
- If you’re running an online store, secure your WooCommerce site with specialized protections for payment processing and customer data.
- Beyond your pages, protect customer communication by securing your forms with password protection that safeguards both user and business information.
- Lock down your premium content with content protection plugins that prevent unauthorized access to member-only resources.
- Perform regular security audits to catch vulnerabilities before attackers exploit them and maintain protection over time.
- Compare firewall solutions: Sucuri vs SiteGround vs Cloudflare to choose the web application firewall that fits your security requirements.
- Don’t have time for maintenance? Explore WordPress maintenance services that handle security updates, monitoring, and optimization for you.
These resources turn your security foundation into a complete fortress. Smart business isn’t just protecting what you have – it’s staying ahead of threats you haven’t faced yet.

Comments Leave a Reply